By: Andy Davis, Research Director, NCC Group.
In 2015 we saw unprecedented levels of publicly released cyber security research into vehicle systems; almost every month a new announcement was made by security researchers at hacker conferences about a different element of the connected car attack surface being targeted. I was part[1] of that wave of research, which is still accelerating at great pace. One of the most important, recurring themes highlighted in many of these research projects was the importance of segregation between infotainment and cyber-physical vehicle systems. The infotainment system that the vehicle occupants interact with either physically or via wireless networks, such as Wi-Fi and Bluetooth, presents a huge attack surface for the modern connected car due to the number of exposed interfaces and media codecs supported. Where telematics solutions interact with infotainment to provide services such as Internet access via the mobile network, that attack surface is sometimes exposed to malicious users anywhere on the planet. When inadequate segregation exists between these highly connected systems and vehicle control systems on the CAN bus, such as braking and steering, attackers who have successfully compromised a head unit can pivot their attacks toward these more sensitive systems, severely impacting vehicle safety. Therefore, the infotainment system and the cyber-physical systems should be highly segregated to ensure that vehicle safety cannot be affected by the compromise of the head unit.
Current segregation methods
As there are currently no public cyber security standards[2] that exist to guide OEMs and their suppliers as to the best way to design and configure vehicle systems in a secure manner, there are a whole range of different connectivity approaches that have been adopted by the automotive industry. These range from no segregation i.e. direct connectivity to the CAN bus from the infotainment system, to the use of a message bus systems such as D-Bus[3], through to “CAN Gateway” modules that are functionally equivalent to a network firewall.
The rise of ADAS
Over the years as vehicles have become more and more “aware” of their surroundings through the use of various sensor technologies, Advanced Driver Assistance Systems (ADAS) have leveraged these sensors to increase driver safety. ADAS functionality within a modern vehicle typically comprises some combination of the following:
- ACC – Adaptive Cruise Control
- AEB – Autonomous Emergency Braking
- BSM – Blind Spot Monitoring
- LDW – Lane Departure Warning
As more and more functionality (including ADAS) has been added to vehicles over time, the dashboard has become increasingly cluttered with buttons, which in turn has increased driver distraction, potentially impacting safety, so OEMs in recent years have tried to de-clutter the dashboard and integrate the control of as many features as possible into the infotainment system.
Below are some statistics provided by SBD[4] (an NCC Group partner company) about a selection of vehicles that constitute a representative sample of modern connected cars with ADAS features. The brands include a mix of prestige and standard vehicles from Europe, Asia and the US. The study investigated how ADAS features were controlled within each vehicle, by the use of physical buttons or via the infotainment system.
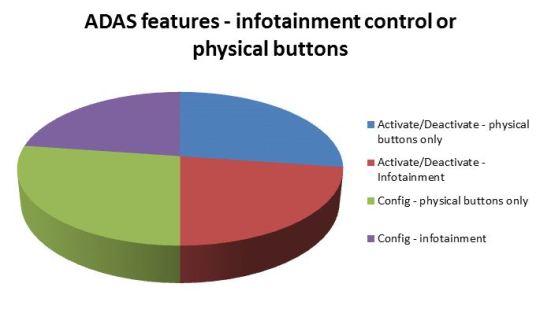
The study revealed that 42% of vehicles with ADAS features allow some form of control of them via the infotainment system e.g. ADAS features could be configured and/or activated and deactivated via the head unit.
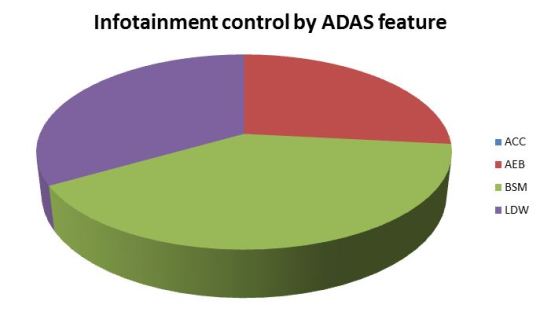
33% of the head unit-controllable ADAS systems could control AEB, 50% could control BSM and 42% could control LDW. None of the vehicles investigated would allow ACC to be controlled by the head unit.
Conclusions
If ADAS features have been integrated into the infotainment system then functionality such as Autonomous Emergency Braking needs to be able to affect a cyber-physical system (the brakes) directly from the infotainment system. Therefore, if an attacker has managed to remotely gain unauthorised access to the infotainment system, even if rigorously implemented segregation prevents them from pivoting their attack to the CAN bus, because functions that control ADAS features exist on the head unit they just need to execute that functionality in order to e.g. disable AEB without the driver’s knowledge.
The security impact of design decisions such as the integration of ADAS into the head unit would be highlighted during the process of Threat Modelling, a core component of a Secure Development Lifecycle, or SDL[5]. There is widespread agreement amongst the cyber security community that the best approach to vehicle systems development is one that adopts the concepts of an SDL, which essentially considers cyber security at all stages throughout the development lifecycle of a product or system. This increases the overall security of the system and reduces the chances of a design-level security flaw being highlighted during testing after the system has been fully developed, which could result in either a costly re-design or a bolt-on security solution that may not be completely effective in mitigating the risks associated with the flaw.
[2] Some cyber security guidance such as SAE J3061 is currently in development, but the scope is still small


Written by harrychapman123
Leave a comment